Phishing is one of the most common methods of online fraud. Scammers impersonate various companies and institutions to deceive unsuspecting victims into divulging sensitive information such as personal data, logins and passwords, or even payment card numbers.
Phishing takes on various forms. It could be a fake bank website that closely resembles the true one, or an email that appears authentic but is designed to deceive. Phishing emails often contain links to fraudulent websites. In the following article, we will explore examples of phishing and methods for detecting attempts to steal data.
Methods for detecting phishing in email messages.
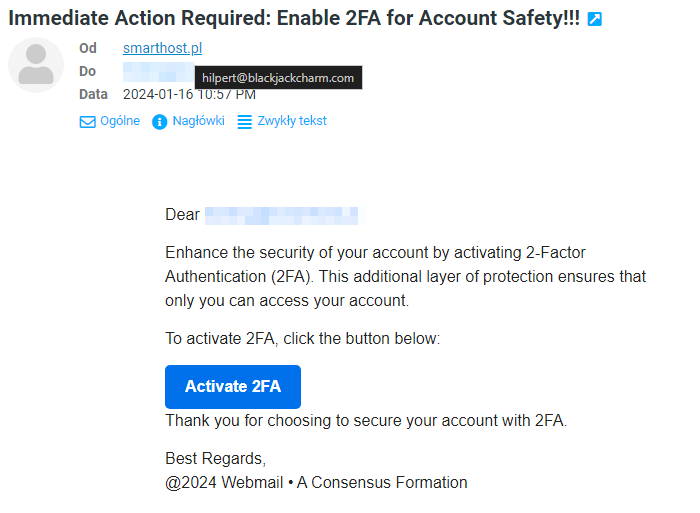
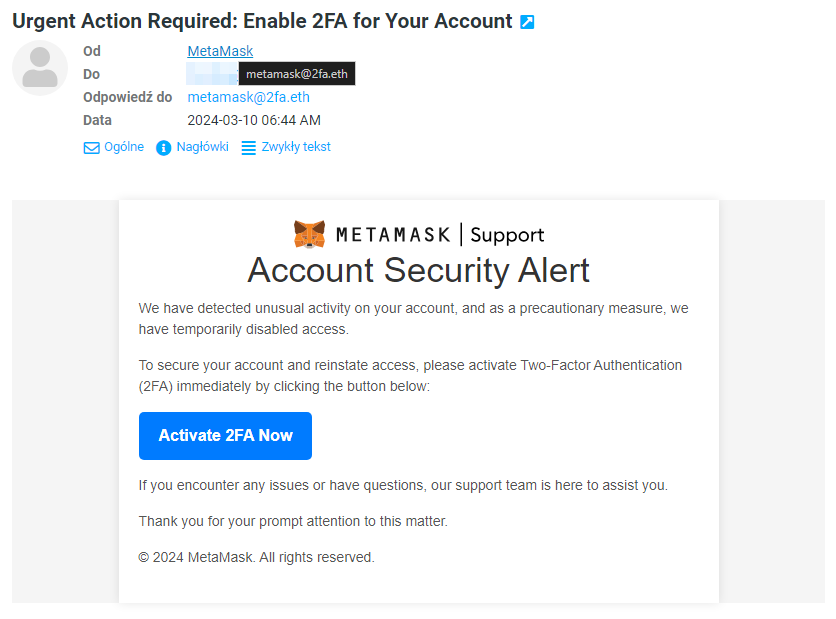
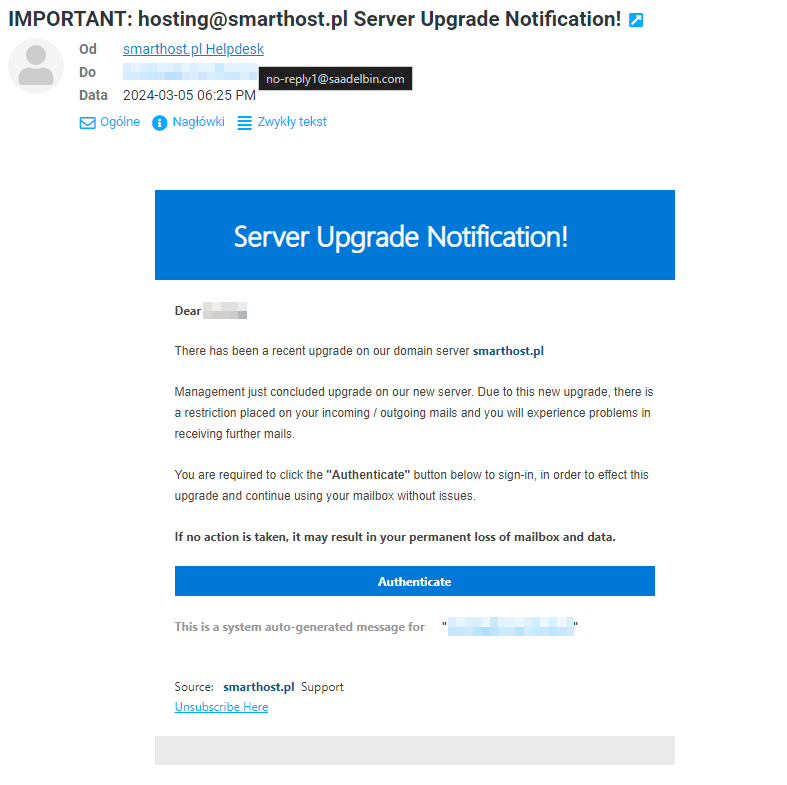
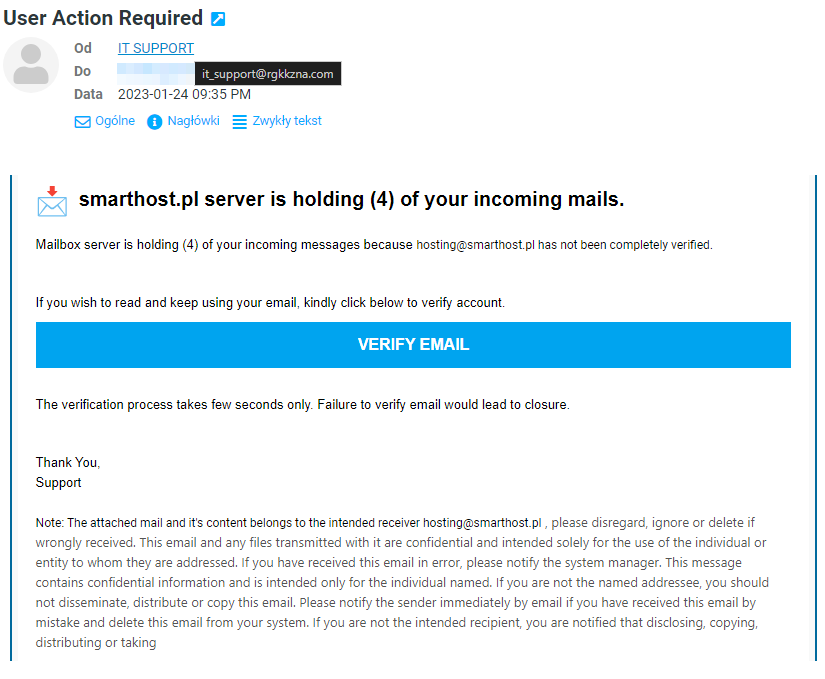
Check the sender’s name and email address: Scammers often impersonate well-known companies or institutions using similar or even identical names and email addresses. However, careful checking of the sender can reveal subtle differences, such as typos or additional characters, which indicate a phishing attempt.
Verify the content of the message: Phishing emails often contain requests for urgent action to prompt you into making hasty decisions. Be cautious of emails that threaten consequences or promise rewards for immediate action.
Avoid clicking on suspicious links and attachments: Scammers often place links to phishing websites or malicious software in attachments. Do not click directly on links or open attachments from emails where the sender seems suspicious. You can check the URL address that the link leads to by hovering your mouse cursor over it to ensure it is authentic.
Verify email headers: Email headers often contain data that can help you verify their authenticity. In the Roundcube email inbox, you can easily check them. Simply go to your inbox, open the selected email, and then click on “headers.” What are the essential elements to focus on?
“From”: The address displayed in the “From” field is presented by the email client as the sender’s address. Fields such as Return-Path or Reply-To contain addresses used, for example, to receive return messages.
These addresses can be easily manipulated by scammers, so they should not always be trusted. However, it’s worth checking them; sometimes they can be email addresses operating in suspicious domains unrelated to the email sender.
“Authentication-Results”: In this section, you will find the authentication report for the message. Pay attention to parts related to SPF, DKIM, and DMARC.
SPF is a method for authenticating the server sending the message. If the headers contain the segment “spf=pass,” it means the message was sent from a server authorized to send emails for that domain.
DKIM is an email authentication method that allows senders to prevent email content from being altered during the delivery process. If the headers include “dkim=pass (signature was verified),” it means the message originates from the domain specified in the “DKIM Signature.”
DMARC is another authentication method that complements SPF and DKIM. It checks how well the From: header aligns with the sending domain specified by SPF or DKIM. The segment “dmarc=pass” indicates that the message successfully passed DMARC verification.
“Spam score”: The content of the message is analyzed by spam detection tools, which assign positive or negative points based on the content. The total score determines whether a given message is recognized as spam.
“X-Mailer”: This section provides information about the email client used to send the message.
Below is an example of such an email message.
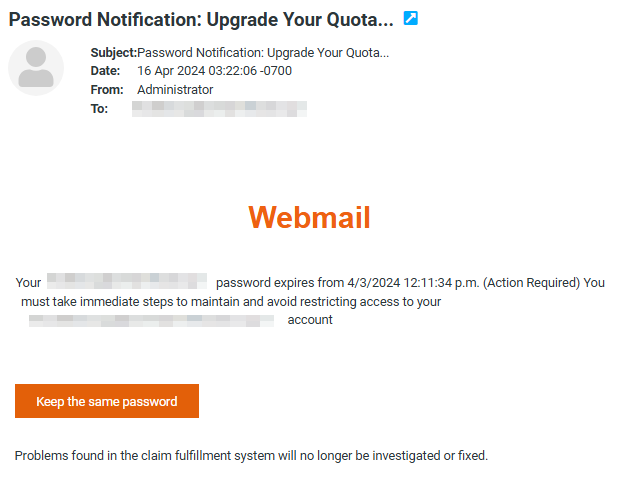
At first glance, you can notice that:
– The subject of the message mentions an alleged lack of space, while the content of the message talks about the expiration of the email password.
Such messages often have inconsistent content.
Users who use webmail can hover their mouse over the address visible in the ‘From’ field to see what email address is listed in the FROM field. E.g.:
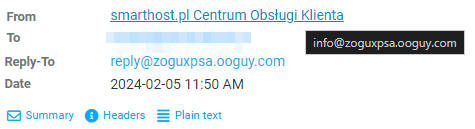
You can notice that the email address provided here is in no way associated with us.
Here is how it appears in the email headers:
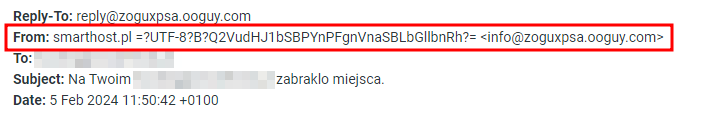
Additionally, if the message contains any links or buttons, please DO NOT click on them. They lead to external sites where you will be asked to enter your login and password.
When you hover your mouse over such a button, the URL to which you will be redirected after clicking will be displayed in the bottom corner of the browser.
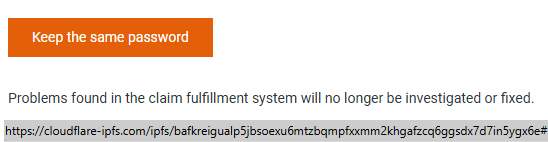
As you can see, the link directs to an external site. Our address, https://smarthost.au, is not included here.
Other examples of phishing emails:
How to check if a website is authentic:
Check the SSL certificate: When visiting a suspicious site, check if it is secured with an SSL certificate. You can do this by looking at the browser’s address bar. If the site is secure, you will see a green padlock icon next to the URL, and the address will begin with “https” instead of “http.” The absence of an SSL certificate might indicate that the site is a scam.
Evaluate the website’s appearance: Phishing websites are often created hastily. Pay attention to unusual design errors and the presence of typos. Compare the site’s appearance with the official website of the company or institution to identify any discrepancies.
Check the URL: Pay attention to the URL of the site that the link redirects you to. Scammers often use similar but not identical addresses, which may contain typos or additional characters. If something seems suspicious, it’s better to avoid clicking on links and entering your information
- RoundCube – Webmail in Your Browser - September 4, 2024
- PrestaShop 8 – Configuring Email Sending with SMTP Authentication - September 4, 2024
- Joomla 3 – Configuring Email Sending with SMTP Authentication - September 2, 2024

