On Smarthost servers, security measures have been enabled to prevent brute-force attacks targeting WordPress. The security protects the wp-login.php address (login screen) and the xmrpc.php file (WordPress remote management). By enabling such security, a WordPress hack attempt will be interrupted by the need to enter reCaptcha.
In practice, it looks like a user who wants to log in to the panel and knows the login and password will do it without any problems, when entering the administration panel page, he will see a standard login field:

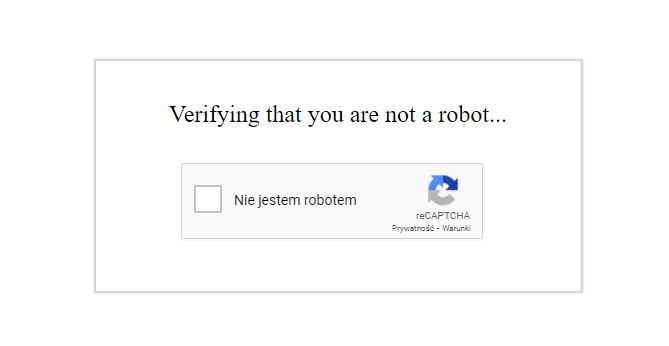
A person / robot who is entering random passwords after 10 unsuccessful attempts within 5 minutes will see a field with a request for verification:
Latest posts by Tomasz (see all)
- Clearing redis cache memory - December 22, 2022
- Does “Time to first byte” (TTFB) means server speed? - October 31, 2022
- Automatic WordPress login security by reCaptcha - August 24, 2021

